1. Introduction
On February 21, 2025, crypto-asset exchange Bybit was hacked and lost over US$1.5 billion in ether tokens (ETH), with the hack widely attributed to North Korea’s Lazarus Group.
This joint case study, prepared by data teams from blockchain data provider Allium and blockchain intelligence firm ChainArgos, expands on the differing approaches to analyzing the aftermath of the Bybit hack.
First, this case study will look at how Allium’s cutting edge blockchain data, enables cross-chain analysis to detect how Lazarus Group effectively laundered stolen funds through multiple DeFi protocols.
Then, building upon the initial analysis, this case study will demonstrate how asking a different set of questions, particularly regarding the role of THORChain in laundering the stolen funds, can provide investigators with better insight, and inform their response to such events.
ChainArgos uses tools designed primarily for financial analysis of blockchain transactions, and using such tools, this case study will demonstrate how:
- a significant spike in activity should have instantly alerted observers to the fact that funds from the Bybit hack were being laundered through THORChain;
- many of wallets that received funds from the Bybit hack were funded and anonymized by some kind of service provider; and
- many (if not all) the proceeds of the Bybit hack can be traced, but that transparency cannot be leveraged in the absence of the appropriate tools.
2. Cross-Chain Analysis and DeFi Link
While many reports detailed how THORChain, ParaSwap, and token transfers were used to launder funds, Allium analyzed cross-chain DeFi (decentralized finance) and DEX (decentralized exchange) activity to uncover an untold part of the story – how the Lazarus Group used DeFi aggregators to discreetly swap US$386 million through DeFi protocols.
Though Lazarus laundered one-fifth of the stolen funds (US$263 million) through PancakeSwap alone, this is the first report on the Bybit hack to highlight the protocol (at the time of writing) and the overarching role of aggregators.
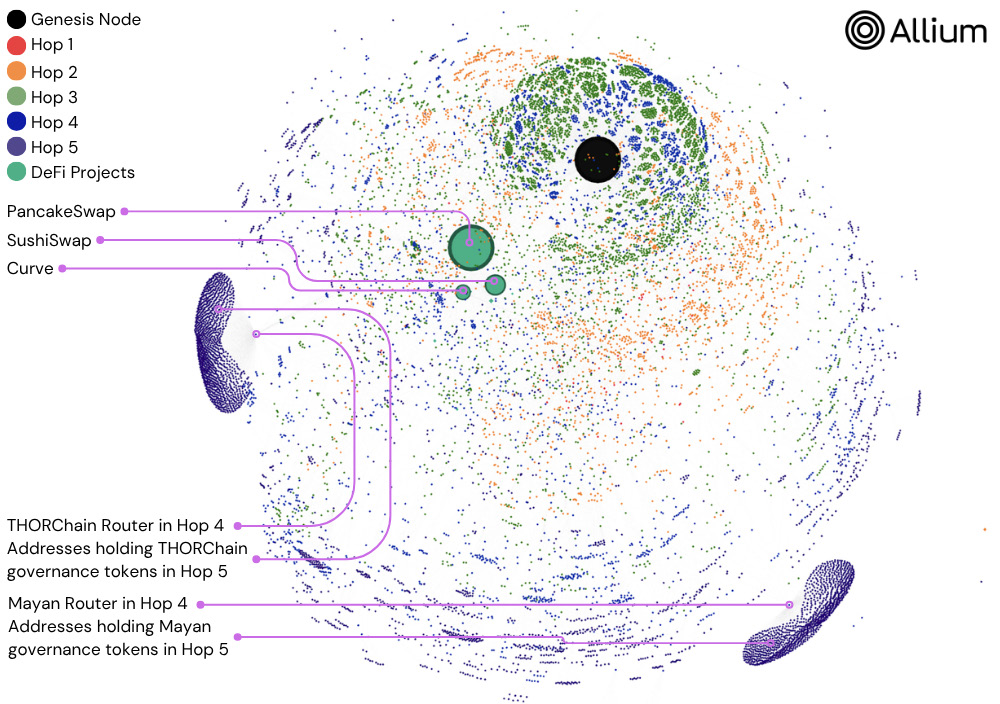
Figure 1. Graph visualization of Allium's cross-chain data, enabling data wizards to track and visualize every interaction within five layers of transactions on Ethereum. (Source: Allium)
Allium’s cross-chain data enables data wizards to track and visualize every interaction within five layers of transactions on Ethereum and the analysis involved:
- 13,000 unique wallets,
- 127,000 transactions,
with a cumulative volume of $12 billion,
- 5 hops away from the genesis node.
DEX Swaps1 Make Recovery more Challenging and Liquidity more Available
DEX swaps make asset recovery more challenging by dispersing funds across multiple assets, requiring victims and authorities to contact each project separately for freezing.
Additionally, swapping a large amount of one asset for smaller amounts of multiple assets allows attackers to access more liquidity pools to cash out stolen funds.
1 A crypto swap is a transaction that results in the direct exchange of one crypto for another, without the need for an intermediary to facilitate the trade. Trading on a centralized exchange is facilitated by an intermediary that exchanges your crypto on your behalf. Swapping on a decentralized exchange (like Uniswap Protocol) uses smart contracts to execute your swap, so there is never a third party in control of your funds. (Source: Uniswap).
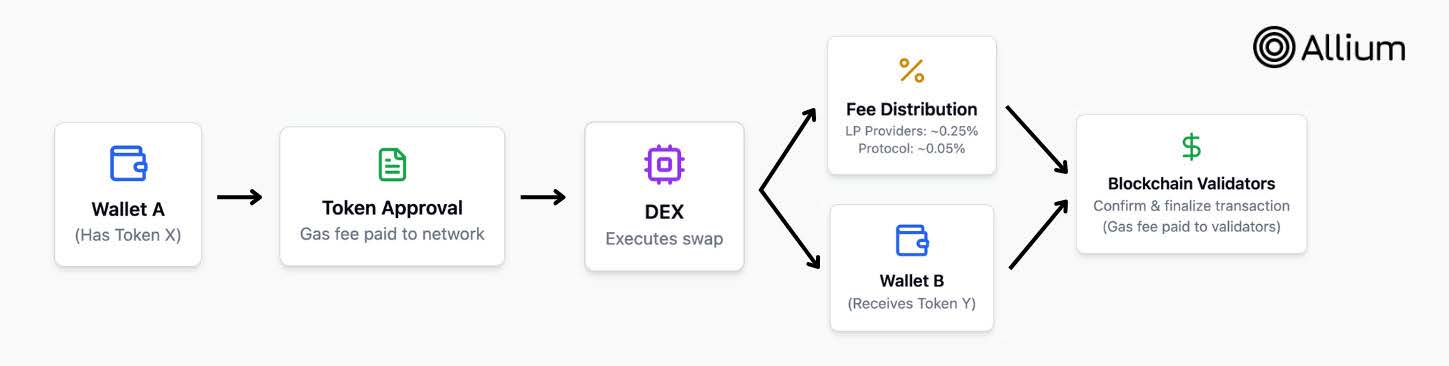
Figure 2. Basic anatomy of a DEX swap. (Source: Allium)
DeFi aggregators bring together trades across various decentralized finance platforms into one place. They aim to optimize trades by pulling competitive prices from across the DeFi landscape. DeFi aggregators permit users to analyze and combine other users’ trading strategies, which could potentially make the process more efficient and user-friendly.
| DeFi Project | USD Volume |
|---|---|
| PancakeSwap | $263 million |
| SushiSwap | $74 million |
| Curve | $47 million |
| Uniswap | $39 million |
| Fluid | $10 million |
| DeBridge | $3 million |
| Across | $2 million |
| Polygon | $836,000 |
| Symbiosis | $326,000 |
| Arbitrum | $9,000 |
DeFi Projects Enable Attackers to Launder Assets Pseudonymously
DeFi projects are used for laundering because they do not require KYC (Know Your Customer) verification to transact, creating a pseudonymous environment where attackers can directly interact with smart contracts.
While the IRS recently mandated that front-end DeFi platforms enforce KYC for tax reporting purposes, these regulations won’t be enforced until 2027.
Instead, DeFi projects check an address’s history to determine transaction eligibility.
However, these addresses must be flagged manually, and most data providers are too slow to support real-time transaction validation. To identify fraud-connected wallets in real-time, organizations need data that clearly shows all DEX and aggregator activity such as provided by Allium.
Conversely, centralized exchanges (Coinbase, Binance, and Bybit) implement AML (Anti-Money Laundering) controls similar to traditional banks. They require KYC verification, monitor transactions for suspicious patterns, and report unusual activities to regulators – creating clear audit trails linking blockchain addresses to verified identities.
Nonetheless, could an inexplicable surge in activity on a DeFi platform have alerted its operators of potential issues and anomalies?
3. The Surge in THORChain Activity
While certain protocols might introduce complexity or require more diligent investigation, the underlying data on the blockchain remains accessible and analyzable if approached in the appropriate manner.
Without any further investigation, and without having ever tagged a single Bybit hacker address, the surge in ETH deposits into THORChain, in excess of the average deposit, should have immediately raised questions for anyone monitoring blockchains in general.
The Bybit hack occurred on February 21, 2025, and by the very next day, deposits of ETH to THORChain saw a 58% surge. By February 23, 2025, ETH deposits to THORChain increased by 155%.
This significant and unmistakable increase in ETH deposits to THORChain is obvious from Figure 4.
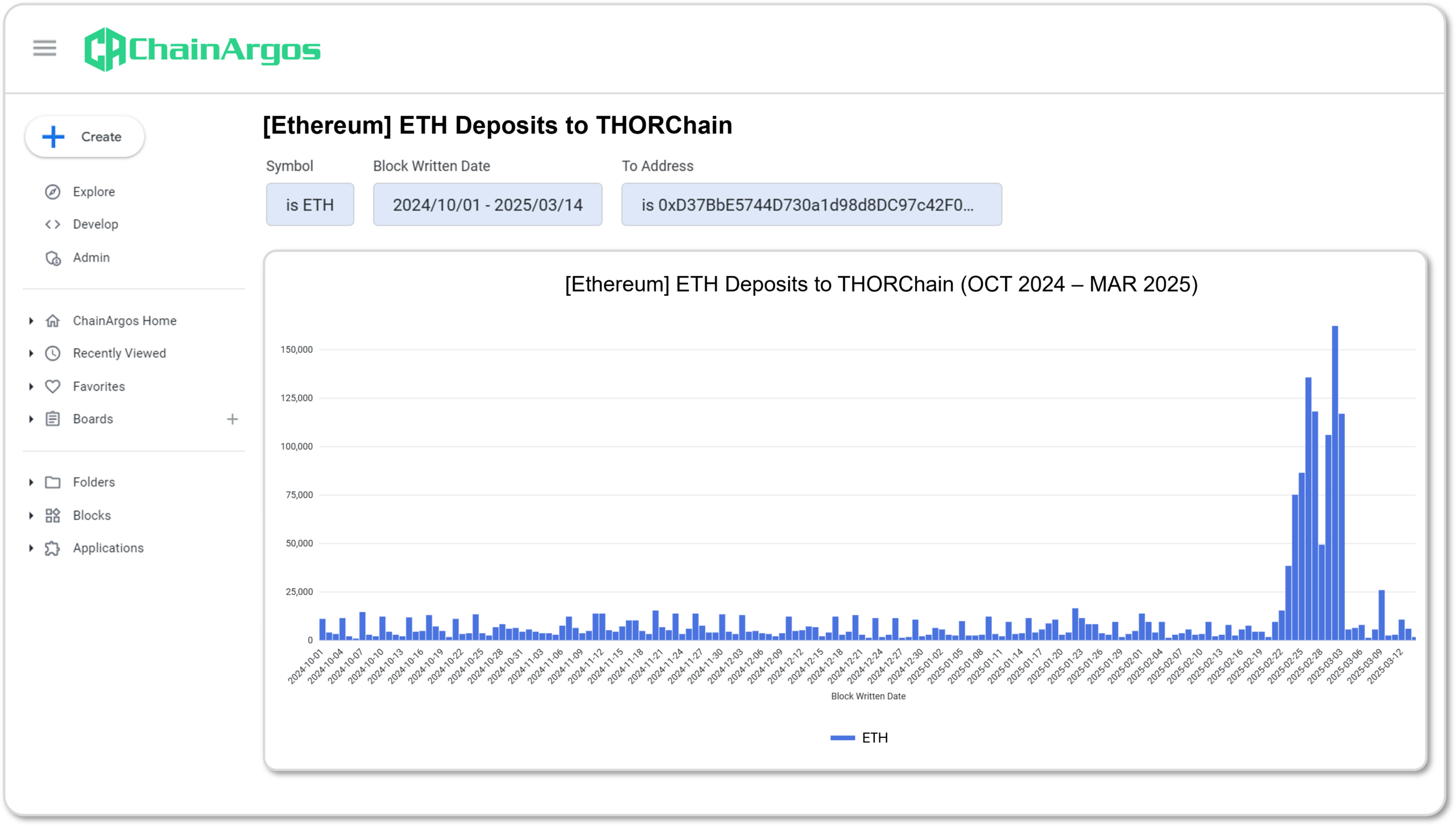
Figure 4. ETH deposits to THORChain from October 2024 through March 2025. Notice the significant rise in ETH deposits immediately following the Bybit hack. (Source: ChainArgos)
When the ETH deposits from the Bybit hacker addresses are superimposed on the same chart in Figure 5., it is even more apparent that almost all of the increase in ETH deposits to THORChain were as a result of the Bybit hackers pushing funds through the platform.
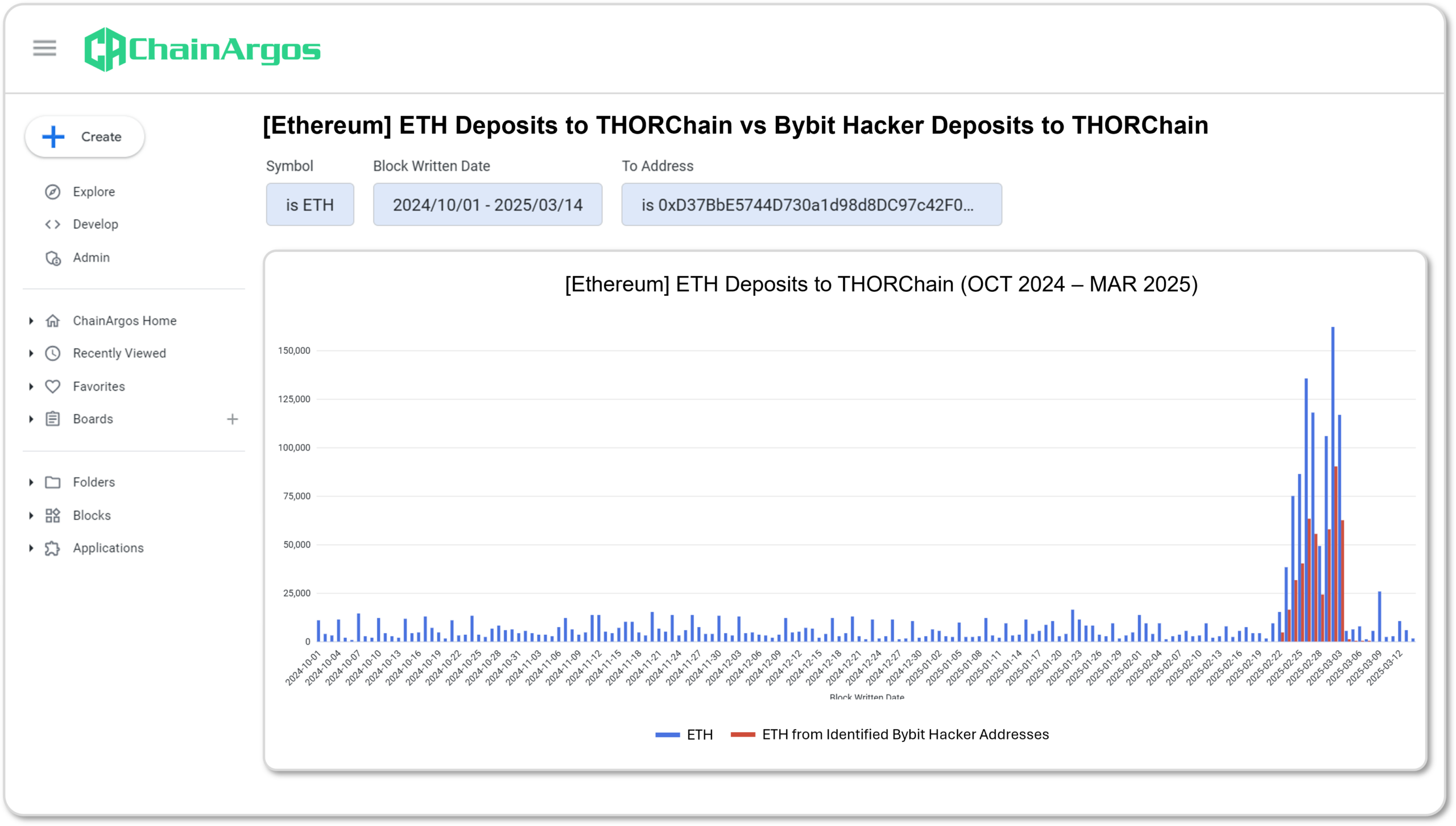
Figure 5. ETH deposits to THORChain (in blue) and ETH deposits to THORChain by identified Bybit hacker addresses (in red). Notice how the ETH deposits by the Bybit hacker addresses almost maps the increase in ETH deposits to THORChain identically. (Source: ChainArgos)
Notice that in Figure 5., the significant increase in ETH deposits to THORChain are almost entirely mapped to the Bybit hacker addresses.
As more Bybit hacker addresses are identified, the gap is expected to close even further, and it would not at all be surprising that the increase in ETH deposits to THORChain are almost entirely attributable to the Bybit hackers making such deposits.
Blockchain transaction activity can change for a variety of reasons, but a sudden increase, especially of the order of magnitude as seen by THORChain immediately after the Bybit hack could have been noted by both law enforcement and regulators.
Previously, ChainArgos noted how a purported 700% increase in the usage of the Ronin blockchain was in fact as a result of token airdrops, and not because of any genuine economic activity.
Because ChainArgos leverages Allium’s blockchain data and applies traditional financial tools to analyze blockchain transactions, relevant authorities could have been automatically notified of the statistically significant increase in ETH deposits to THORChain, prompting timely investigation and remedial action.
Allium and ChainArgos enable macro analysis of blockchain transactions, allowing regulators and law enforcement agencies to very quickly identify areas of interest and potential investigations.
In the next section, we see how ChainArgos and Allium power micro analysis by investigating a Bybit hacker address and demonstrating how access to such data can ensure that constrained investigative resources are directed to the most effective areas.
Unidentified Service Providers
As identified by ZachXBT, and others, the Bybit Hacker 0x476 Address (0x47666fab8bd0ac7003bce3f5c3585383f09486e2) is one of the main addresses used to receive the proceeds of the Bybit hack.
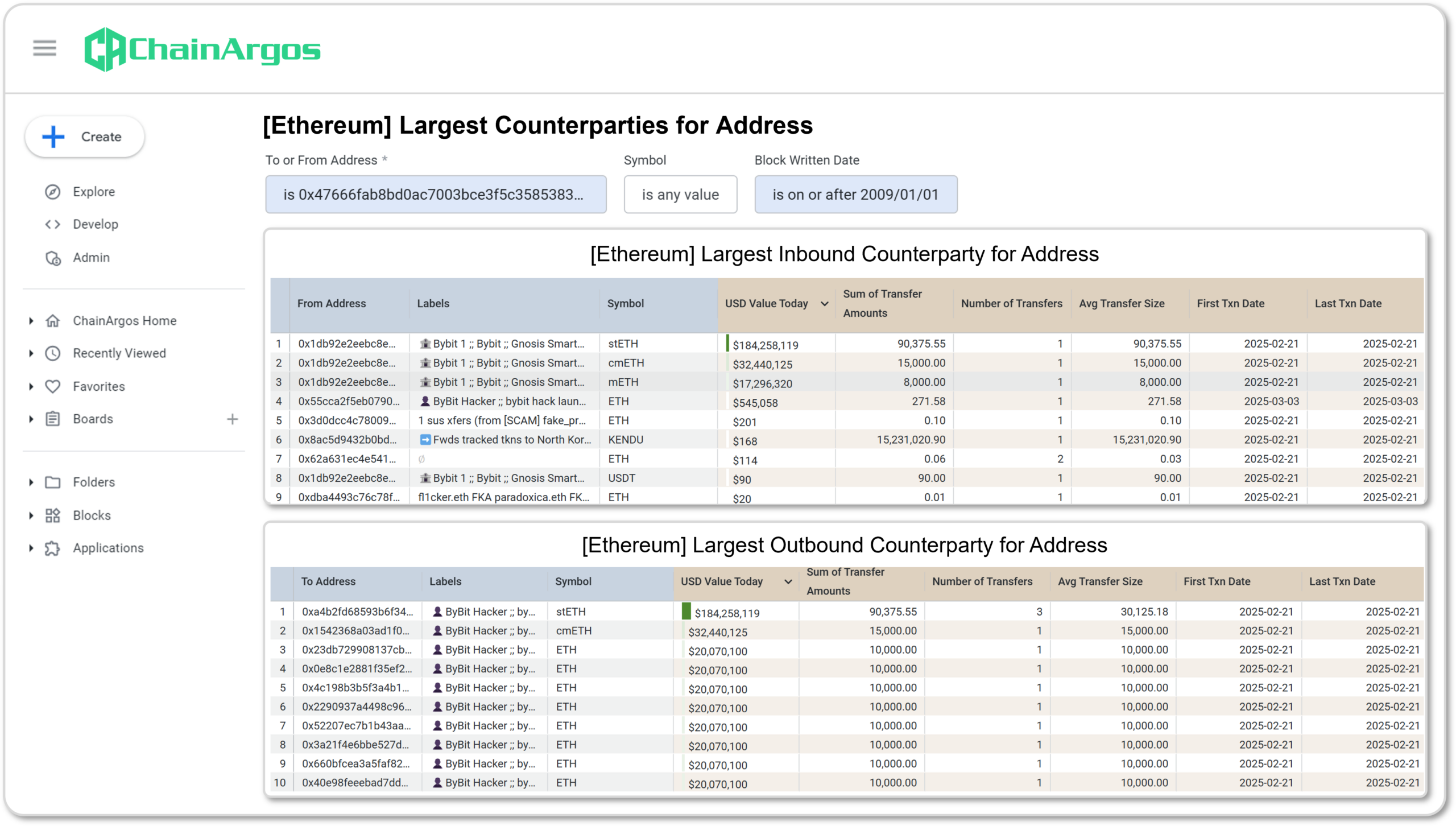
Figure 6. Largest Counterparties for the Bybit Hacker 0x476 Address. Several addresses send token amounts of ETH to the Bybit Hacker 0x476 address on February 21, 2025, and we will examine the 0x62a address which sends 0.06 ETH to the Bybit Hacker 0x476 address. (Source: ChainArgos)
We can see from Figure 6., that Bybit Hacker 0x476 Address is one the main addresses that receive stETH, cmETH and mETH from identified ByBit wallet addresses.
Notice however that the Bybit Hacker 0x476 Address itself receives a token amount of 0.06 ETH from the Service Provider 0x62a Address (0x62a631ec4e541e7b7de90e7be01f09b88f67126) on the day of the Bybit hacking, February 21, 2025.
Outside of this token transfer of ETH (pun intended), the Service Provider 0x62a does not interact with the Bybit Hacker 0x476 on any other occasion.
The transaction of ETH from the Service Provider 0x62a Address to the Bybit Hacker 0x476 Address immediately stands out because the transfer of 0.06 ETH is small enough to create a reasonable inference this is for the provision of gas fees and informs the next step of our investigation.
Analyzing the transaction activity of the Service Provider 0x62a Address in Figure 7., it becomes immediately apparent that this address does not just provide gas fees to the Bybit Hacker 0x476 Address, but a slew of other addresses associated with the Bybit hack as well.
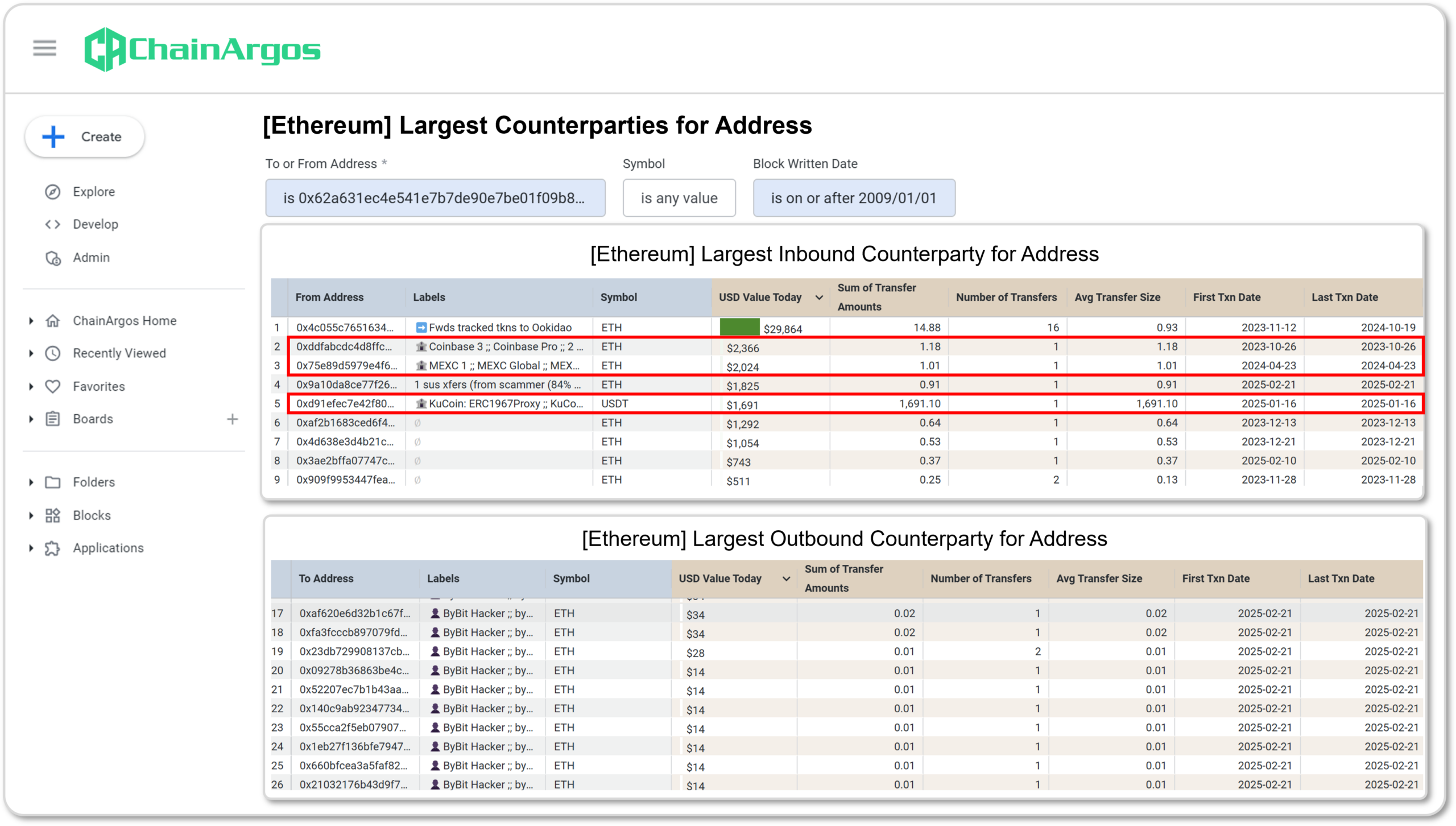
Figure 8. Largest Counterparties for the Service Provider 0x62a Address. The various crypto-asset exchanges from which the Service Provider 0x62a Address has received crypto-assets from has been highlighted. (Source: ChainArgos)
Typically, exchanges facilitate the transfer of crypto-assets from the exchange’s wallet addresses to external addresses only after they have been “whitelisted” or proved to belong to the owner of the account with that exchange.
In Figure 8., it would stand to reason that Coinbase, MEXC, and KuCoin would be in possession of the requisite know-your-customer documentation of whoever controls the Service Provider 0x62a Address.
With this information, investigators could query the owner of the Service Provider 0x62a address as to why they provided gas fees to the various Bybit hacker wallet addresses, or if they were providing such pre-funded wallets as a service.
In the past, one of the easiest ways to anonymously fund an Ethereum wallet was to mine ETH, essentially making the source of funds of such a wallet “untraceable.”
As Ethereum moved to Proof-of-Stake, such anonymization methods became less practicable and in the wake of this shift, a cottage industry of service providers emerged to provide such anonymization services, often using ETH that had been mined a long time ago.
It is entirely possible that whoever was operating the Service Provider 0x62a Address did not know the wallets they were funding on February 21, 2025 would be used to receive the proceeds of the Bybit hack.
Nevertheless, identifying such service providers enables authorities to push investigations forward.
4. The Allium and ChainArgos Difference
As more economic activity moves onto the blockchain and as more assets are tokenized, the need for tools that enable effective financial analysis of blockchain transactions grows.
Leveraging Allium’s blockchain data solutions, ChainArgos is able to focus on building effective applications that allow both macro and micro financial analysis of blockchain transactions, enabling unprecedented insight.
- Identify Key Transaction Clusters: Start by identifying the initial outflows of ETH from the known Bybit exploit addresses, then track transactions where significant amounts of ETH were moved, to understand the areas to focus investigations.
- Focus on Counterparties: Look for patterns in the destination addresses of the swapped cryptocurrencies. Are funds being consolidated in a few addresses? Are these addresses known to interact with specific service providers? Small transfers shouldn’t be ignored and can often provide insight into previously unidentified service providers, or unexpected relationships.
- Financial Analysis: As demonstrated from the Bybit hack, tracking and tracing the flow of hacked proceeds alone does little to advance safety or security on the blockchain. Instead, a combination of macro and micro financial analysis helps identify service providers such as Service Provider 0x62a, creating a potential weak point that authorities can leverage to break apart such networks that facilitate illicit activities.
Blockchain intelligence doesn’t need to be complicated. Because one of the fundamental goals of any blockchain transaction is the transfer of value, blockchain transactions need to be viewed through a financial lens, to deliver actionable insight.
What is the economic purpose of a transaction? Who is providing the wherewithal to facilitate that transaction and what means are they using?
Working with Allium, ChainArgos is powering an entirely different approach to blockchain intelligence, putting in the hands of analysts and investigators powerful tools for financial analysis, to enable the uncovering of key players, service providers, and relationships that would otherwise have gone unnoticed.
